

In today’s cybersecurity landscape, hash cracking poses a significant threat, potentially exposing sensitive information, including passwords, messages and documents. Storing passwords in plain text is insecure, as unauthorized users can easily access them, leading to significant data breaches.
Hashing is a cryptographic technique that converts data into a fixed-size string, ensuring security by verifying data integrity. It acts as a form of authentication, allowing systems to compare hashed values without exposing the original data.
Below is an example of a hashed password using the MD5 algorithm, incorporating the keyword PteraTch. This demonstrates how hashing transforms sensitive data into a secure format, ensuring that even if the hash is exposed, the original information remains protected.

Hashing algorithms have long been fundamental to data security. Designed to be computationally infeasible to reverse-engineer, they play a critical role in password storage, digital signatures and data integrity checks. However, advances in computing — particularly quantum computing — pose new threats to traditional hashing techniques, making future-proofing methods more important than ever.
Hashing algorithms are widely used to protect businesses and sensitive data in various areas, including:
As computing power advances, the security of hashing algorithms faces increasing challenges. This article explores how long it takes to crack an 8-character hash using three different setups:
By comparing these setups, we aim to highlight the differences in computational power, cost, and efficiency. Additionally, we’ll provide some recommendations and best practices to help businesses strengthen their cybersecurity against these evolving threats.
The Problem: To assess the impact of computing power on hash security, we simulate an experiment to brute-force an 8-character alphanumeric password.
Key Parameters:
Goal: Crack the hash by brute force — generating every possible combination, hashing it, and comparing it to the target hash.
1. Personal Computer (PC)

Hash Rate (Intel i7, 16GB RAM)
A typical Intel i7 system with 16GB of RAM can handle in the ballpark of 300,000–500,000 hashes per second (depending on exact CPU model, clock speed, and other factors).
Cost Estimate
Notes
2. Google Cloud Server

3. Willow Quantum Chip
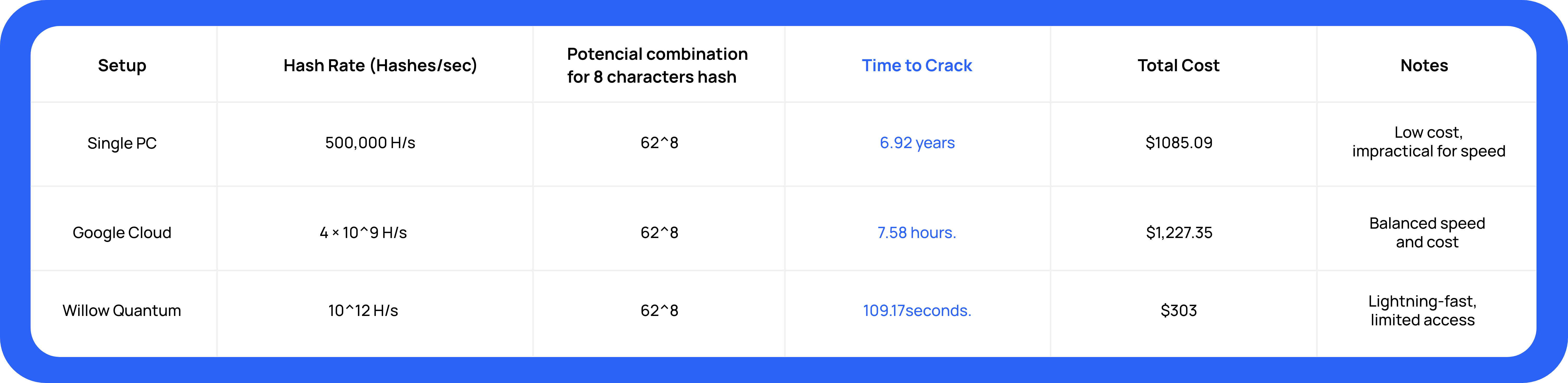
This summary compares the time to crack an 8-character alphanumeric password using three setups:
Here are some recommendations on how you can protect your business against quantum attacks. Quantum computing brings a significant threat to current cryptographic methods. Here are strategies to safeguard your systems:

Quantum computing, exemplified by Google’s Willow chip, marks a new era of computational power, putting once-unbreakable encryption at risk. While classical systems like PCs and cloud servers remain dominant in accessibility, the rapid advancement of quantum technology demands immediate action.
Transitioning to quantum-resistant algorithms, increasing encryption strength, and staying ahead of emerging standards will be critical to securing data in the quantum age.
As quantum computing reshapes cybersecurity, businesses must act now — adopt quantum-resistant encryption, strengthen defenses, and stay ahead of emerging threats. The future of data security depends on the steps you take today. 🔐
If you’d like to explore how Ptera can help secure your business, learn more at https://ptera.tech